Zero Trust in an Application-Centric World
Zero Trust is a powerful strategy that can help a business go faster and be more secure. In recent years it has received a lot of airtime even though it is not a new concept. It’s a concept that’s more relevant and important today than ever, particularly as companies around the world grapple with how to operate and respond during the COVID-19 crisis. Zero Trust was a theme in my recent Agility keynote and a concept that’s critical for every organization to better understand as they accelerate digital transformation initiatives.
Securing the traditional network perimeter (a.k.a., the moat and castle approach) is no longer sufficient. With the rise of applications being deployed in multi-clouds and the growing mobile workforce, the network perimeter has all but disappeared.
Zero Trust eliminates the idea of a trusted network inside a defined perimeter. Today, you must apply least-privilege user access and scrutinize it as much as possible, assume attackers are already on the network and hiding in it, and get more context and visibility from the control points. To enable Zero Trust, organizations must abandon the “Trust, but Verify” approach and now adhere to these three principles:
- Never trust
- Always verify
- Continuously monitor
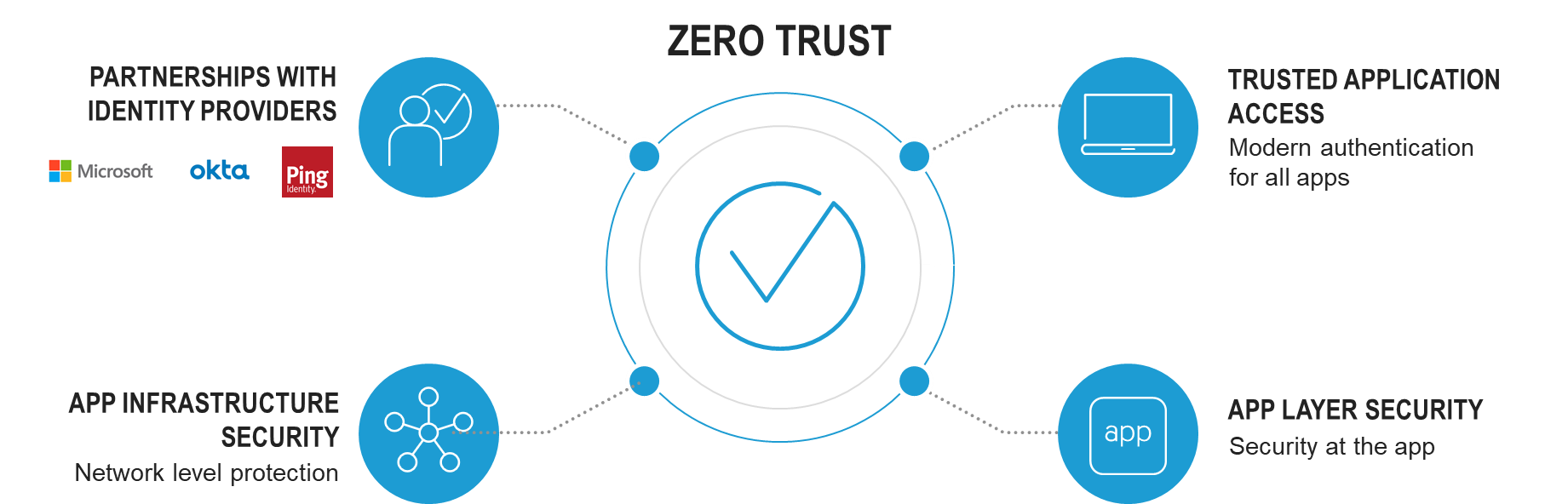
While no vendor can provide everything needed for Zero Trust, F5 can add value with our robust application security portfolio and secure four key control points in a Zero Trust architecture. Specifically:
- The endpoints accessing the applications: our trusted app access solutions provide modern authentication for all apps.
- The network infrastructure: we have application infrastructure security solutions to help protect the network.
- The applications (whether the apps are in the cloud, on-premises, SaaS-based, or fully managed): we offer application layer security solutions to provide security at or near the application and protecting the application stack (from layer 4 through 7).
- The identity service: we have deep partnerships with Microsoft, Okta, and Ping. By integrating our trusted app access solutions with these Identity-as-a-Service (IDaaS) providers, we help to bridge the identity gap between cloud-based, SaaS, and mission-critical and custom applications to offer a unified, secure access experience for users.
Let’s dive deeper on how F5 can specifically help you deploy a Zero Trust model using these three F5 security solutions: Trusted App Access, App Infrastructure Security, and App Layer Security.
Trusted App Access
When it comes to application access, organizations must assume that everyone accessing their site is a bad actor. Access-related breaches continue to rise. According to F5 Labs, in 2019, access-related breaches represented the largest proportion of the known breach causes at 52%, up from 47% in 2018.
F5 BIG-IP Access Policy Manager (APM) secures, simplifies, and centralizes access to apps, APIs and data, no matter where users and their apps are located. With Identity Aware Proxy (IAP), APM deploys a Zero Trust model validation based on granular context, securing every app access request. It also continuously monitors each user’s device, location, and access throughout app session.
The primary value propositions are:
- A great user experience with SSO and a common user experience accessing all apps, no matter if the app is on-prem or in the cloud
- More secure applications in a Zero Trust architecture
- A common architecture for hybrid environments and common policy across multiple clouds
With the addition of Shape, and the ability to determine bad actors committing fraud, we are now able to better identify good users and reduce the numbers of times the user is required to input a password. This allows the user to get more access to services without forgetting passwords, lowers support costs, and increases the top line.
App Infrastructure Security
The network infrastructure is important to ensure that the apps are secure and available to achieve Zero Trust. One area that could impact your network is around encrypted threats.
Encryption is now the new normal. Based on F5 Labs research, 91% of page loads are encrypted with SSL / TLS. But attackers also use encryption to bypass security controls. Organizations must assume their inbound encrypted traffic is harboring malware. They must also assume outbound encrypted traffic contains sensitive information that can be exfiltrated.
F5 SSL Orchestrator solves the encrypted traffic dangers in your network. It’s a dedicated solution for orchestration of inbound/outbound SSL/TLS traffic and centralizes encryption control. It eliminates security blind spots by exposing malware hiding in encrypted traffic and halts exfiltration of stolen data.
App Layer Security
The reality is that applications are vulnerable in any organization. From F5 Labs research, an enterprise deploys an average of 765 apps. With this many apps in play by one enterprise, attackers know how important they are and actively try to compromise the apps as every single one of them can be a back door (or front door) to valuable intellectual property and data. It’s critical to continuously protect the apps as part of your Zero Trust strategy.
F5 can protect the application stack in a Zero Trust architecture. Our WAF solutions such as Advanced WAF and Essential App Protect help to prevent against common vulnerabilities and exploits such as the OWASP Top 10 or SQL/PHP injections.
Our WAF solutions can also protect against Layer 7 DoS attacks with our behavioral analytics capability to continuously monitor the health of the apps. We also provide credential protection to prevent unauthorized access by attackers to user accounts. Plus, with the growing use of APIs, we can protect them and secure your apps against API attacks.
While F5 protects your application vulnerabilities with WAF and API security solutions, we also protect your business logic from being abused with Shape.
F5 delivers our security offerings to fit an organization’s Zero Trust deployment strategy—self managed, as-a-service, or as a fully managed service via Silverline and Shape Security.
If you’re interested in learning more, you can view my keynote from Agility on-demand, reach out to us for help with your Zero Trust deployment.