The Bots are in Business and Business is Good
By the end of 2022, the forecast is that 65% of global GDP will be digitized. Bots are literally following the money.
As organizations continue to progress on their transformational journey to digital business, attacks and threats have also progressed. Many of them have moved their target “up the stack” to focus on how to exploit business rather than CVEs. Thus, it’s no surprise to see the term “bot” become a standard part of the business vernacular.
While we most often associate the term with software and scripts that launch a variety of attacks, those attacks are generally categorized as technical. That is, we associate bots with DDoS attacks and attempts to exploit known vulnerabilities to gain unauthorized access, plant malware/backdoors, or deny service to consumers.
But increasingly, bots are a part of an abusive army that targets the business and the inherent vulnerabilities of operating a digital presence.
For those unfamiliar with the term, I refer you to Simplifying Security by Stepping Back. A quick refresher if you prefer:
Inadvertent vulnerabilities are those caused by human mistakes. They include misconfigurations, insecure coding practices, choosing speed over security, and removing protections in production to meet a deadline. These often wind up as a CVE and cause a splash on social media.
Inherent vulnerabilities, however, are a different matter. These are vulnerabilities to protocol and logic abuse, vulnerability to attack of services you must provide because there's no other option. DNS, for example, must be public and is often the target of attacks. Not because the implementation (code) has vulnerabilities, but because of its critical role in delivering applications.
A significant percentage of attacks on the business today target inherent vulnerabilities. These include well-known credential stuffing attacks to gain access but also include a growing cadre of business attacks that seek to exploit APIs and the increasingly digital interfaces presented to customers.
For example, a grinch bot attempts to purchase, at high volumes, in-demand products with the intent to resell them at a much higher price. Similar to the practice of scalping event tickets, grinch bots are capable of depleting inventory and depriving consumers of the goods they desire, especially during the holidays (hence the name).
The problem is so pervasive that US lawmakers have introduced a bill—the Stopping Grinch Bots Act—designed to punish digital scalpers who destroy children’s dreams of receiving the latest and greatest toys for Christmas.
The bill is an extension of the Better Online Ticket Sales Act (BOTS Act) of 2016 that criminalized event ticket scalper bots. They are not the first; several governments across the globe have introduced legislation and regulation designed to address the growing problem of bots attacking business, though few have managed to make it into law.
Unfortunately, such measures do not address the biggest challenge business faces in stopping bad actors from employing bots: identifying them in the first place.
Today, identification of bots requires more sophisticated analysis of signals both behavioral and environmental. There is no single signal that definitively identifies a “bot” today, and even valid credentials can’t guarantee a legitimate user behind a transaction. Moreover, that analysis must be performed in real-time to identify—and neutralize—bots before they can become problematic for the business.
So it’s no surprise that security in general leads the conversation when it comes to use of AI and machine learning today. The volume and speed at which digital signals are generated—and the consequences of failing to recognize an attack—point to the use of AI and machine learning, which excels at solving problems where speed and scale are involved.
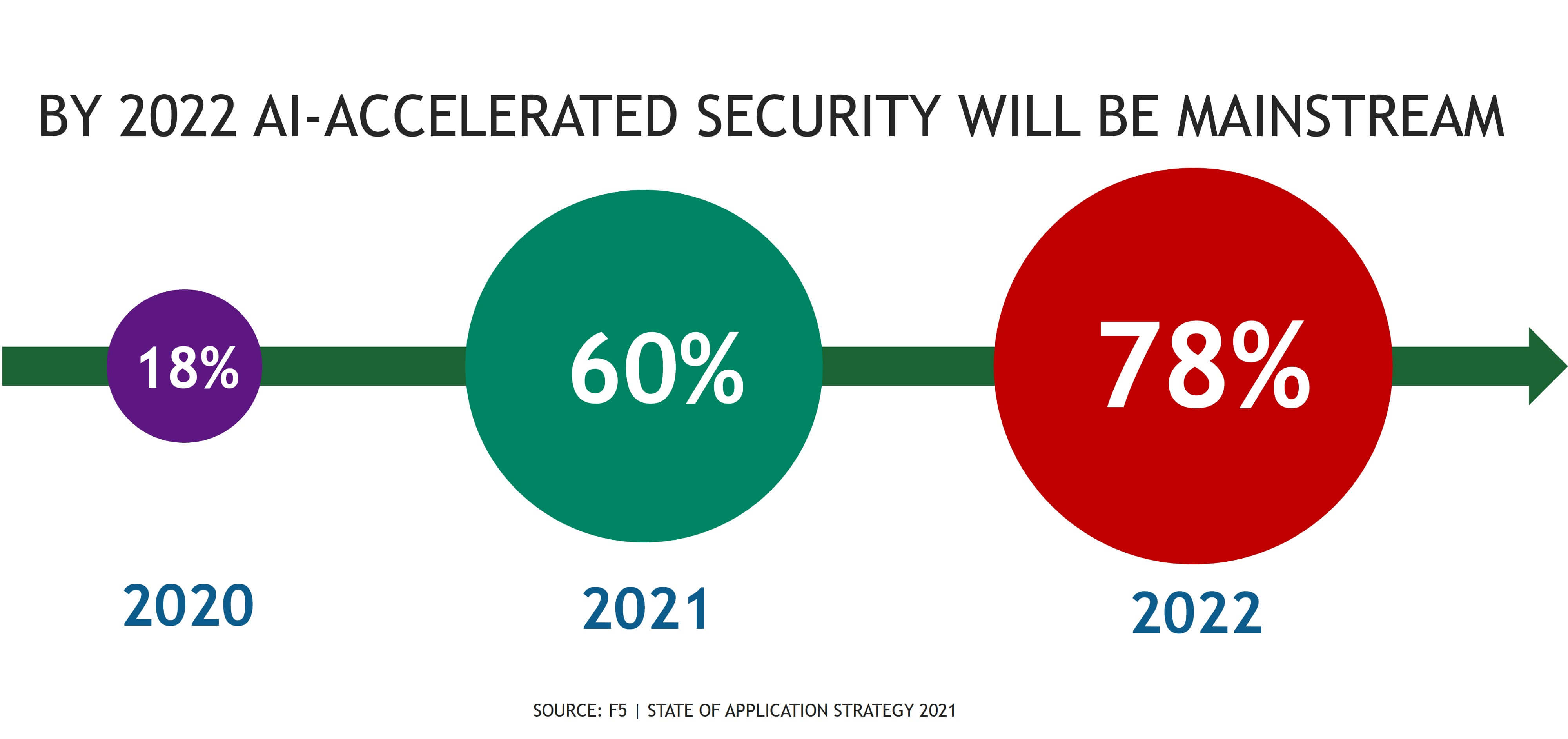
This leads us to one inescapable conclusion: we need to redefine cybersecurity.
Security practices must evolve along with the technology stacks needed to support a digital business. Signals that indicate health—or lack thereof—of a digital business are, by definition, digital too. That is why we’re seeing excitement around IT/OT convergence—the coming together of customer and operational data as well as the rise of data-related roles within IT and the business from data scientists to data ops to Chief Data Officers.
The role of data is increasingly important to securely operating a digital business at scale, and that means evolving our understanding of all the disciplines within technology that rely on it.
