New Study Reveals What’s Driving—and Limiting—TLS 1.3 Implementation
Four years ago, Meghan Markle married Prince Harry. Meanwhile, Sears filed for bankruptcy, and the world was graced with a rare super blue blood moon. Toys “R” Us also closed all its stores, and Apple became the first American publicly traded company to reach $1 trillion in value.
Let’s not forget 2018 also marked the approval of TLS 1.3 by the Internet Engineering Task Force (IETF).
Since then, organizations have had plenty of time to evaluate the benefits and challenges of adopting TLS 1.3, the newest version of one of the most widely used cryptographic protocols that enables data security and privacy for the internet.
To understand why—or why not (yet)—companies have implemented TLS 1.3, Enterprise Management Associates (EMA) prepared the research report, “TLS 1.3’s Fourth Anniversary: What Have We Learned About Implementation and Network Monitoring?”
The EMA study sponsored by F5 includes sentiments from technology and business leaders in North America across industries like technology services, finance, and healthcare. Participants shine a light on how companies are prioritizing information security and compliance priorities, not to mention how regulations for data security and privacy have influenced the direction of security priorities.
Here are three conclusions from the report:
1. Regulatory and vendor controls, improved data security, and remote work drive adoption
Data security and privacy standards have been front-of-mind for business and technology leaders over the past few years. So, it’s little surprise participants in the study indicated improved data security and privacy as primary drivers for implementing TLS 1.3. In fact, 85% of the surveyed individuals indicated data security as the greatest benefit to their TLS 1.3 implementation.
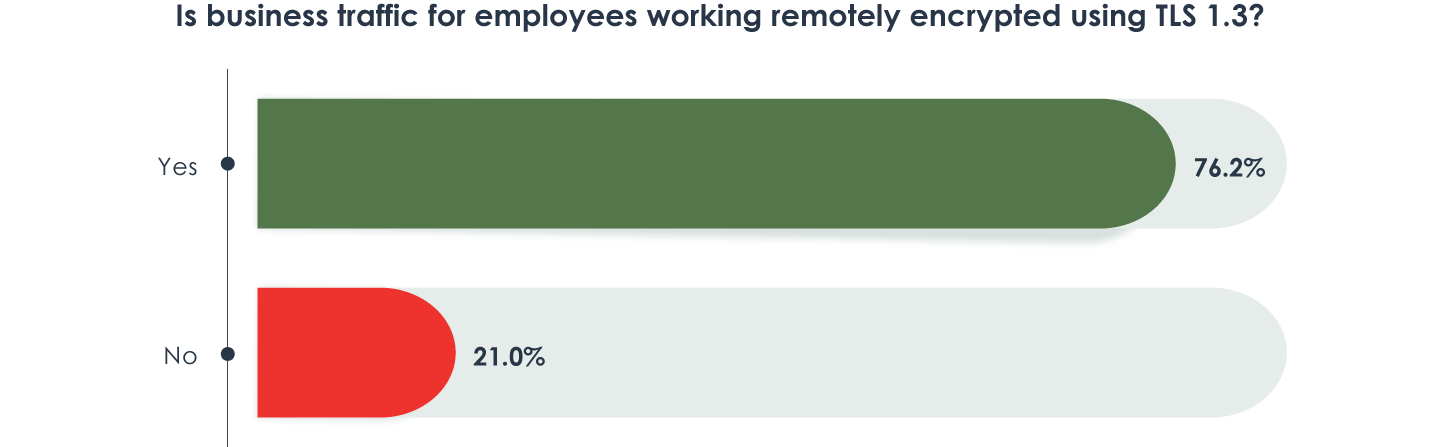
Additionally, as companies adapted to the COVID-19 pandemic, the push towards—and continued staying power of—remote working and the need to safely handle sensitive data and company intellectual property played a role in the adoption of TLS 1.3. As Figure 1 shows, 76% of respondents use TLS 1.3 for business traffic of remote employees.
2. Visibility and monitoring considerations are top obstacles
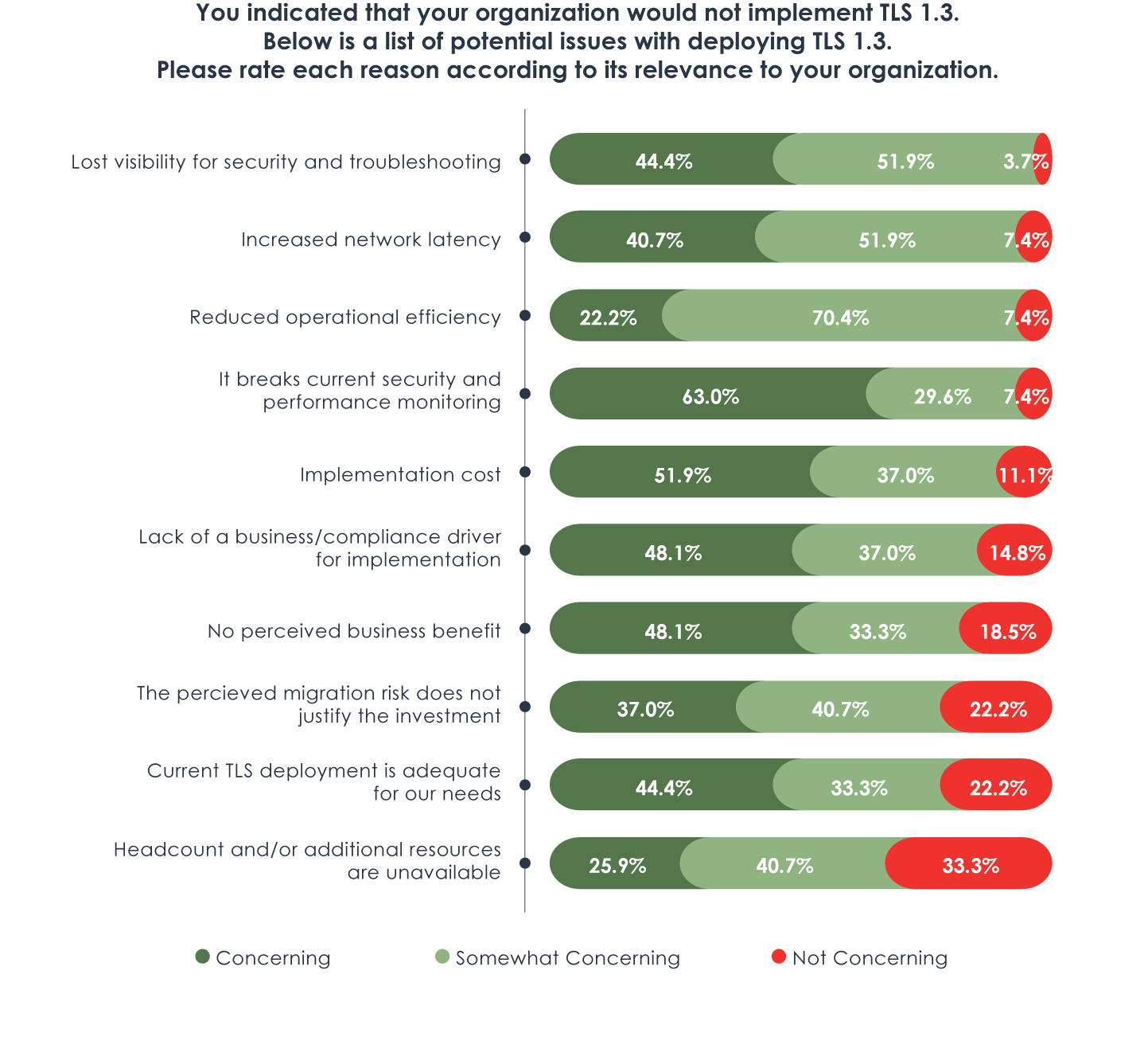
Despite vendor and regulatory controls like HIPAA and the EU’s General Data Protection Regulation (GDPR), organizations are struggling to move forward with TLS 1.3 because of the anticipated impact on security and monitoring plans within their environment, as demonstrated in Figure 2. On top of that, it’s really no secret this type of integration can be challenging. So, instead of making the commitment, many organizations are buying time to map out a migration plan and evaluating stop-gap solutions that are easier and less intrusive to implement than TLS 1.3.
The loss of visibility also creates pause for 96% of the survey participants. After all, 44% of the respondents who implemented TLS 1.3 were forced to roll back their implementation due to loss of visibility into traffic, and over a quarter of respondents believe they may have suffered a security breach because of a lack of traffic visibility with the protocol.
3. Resource and implementation costs are substantial
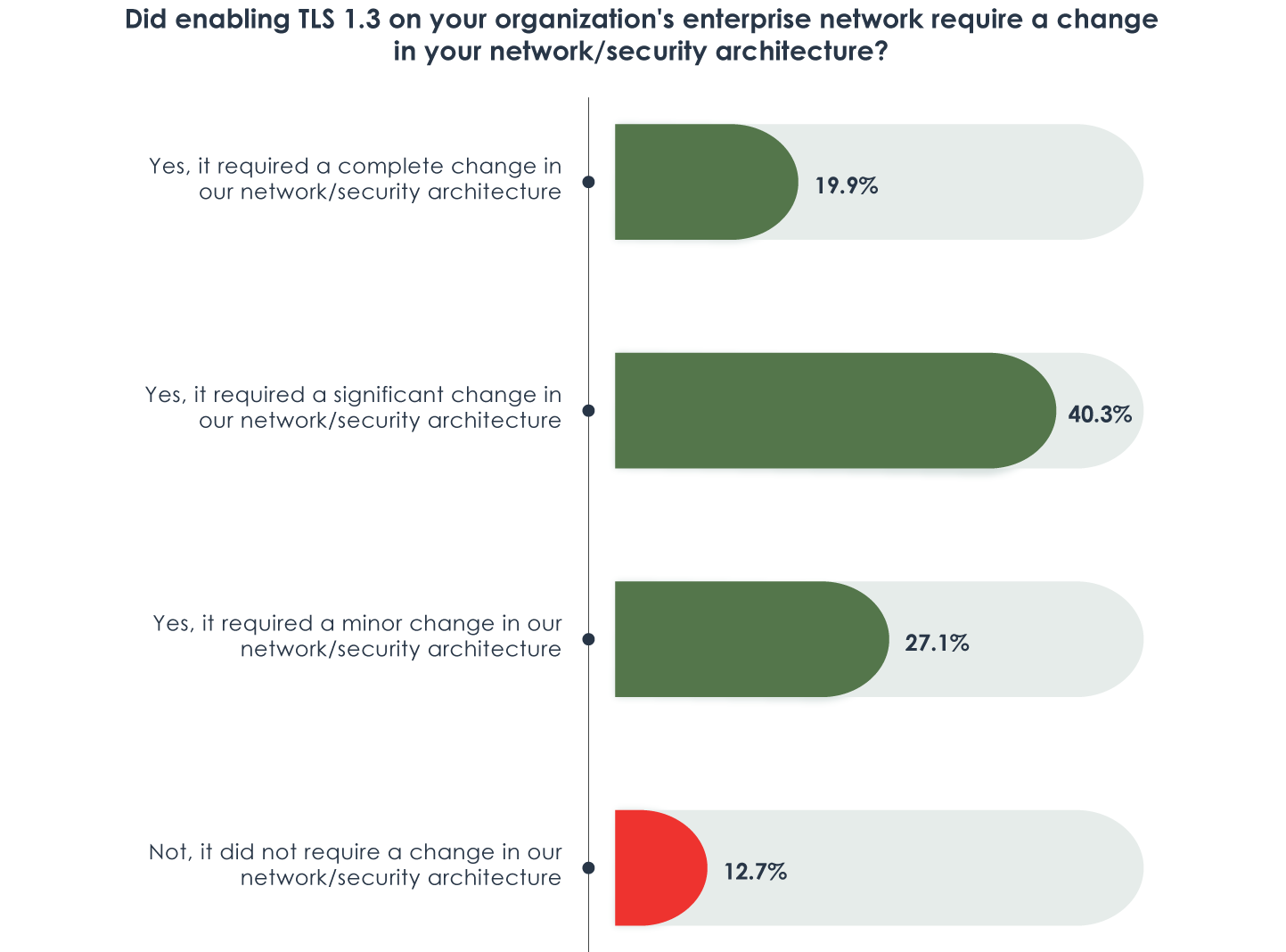
Eighty-seven percent of organizations surveyed that have implemented TLS 1.3 required some level of infrastructure change to accommodate the integration, as illustrated in Figure 3. Updating a network topology is certainly a hard pill to swallow for many. It’s time-intensive and costly. Pulling resources to implement a project of this scale is difficult to justify given limited human resources across an already stretched security staff and its very little perceived business value in comparison to competing business needs (81%).
While several variables will continue to influence the adoption of TLS 1.3, one thing’s for sure—TLS as a recommended data privacy protocol is here to stay.
And with nearly 90% of all internet traffic now encrypted, and that number continuing to grow, what you can’t see can hurt you. Cybercriminals are constantly taking advantage of encrypted traffic to hide malicious payloads, regardless of the TLS version. If you’re not inspecting it, you’re leaving your organization vulnerable.
Learn more about what technology and business leaders say about the implementation of TLS 1.3 in the full EMA report and understand why visibility and orchestration of SSL/TLS encrypted traffic—especially inbound and outbound traffic encrypted with TLS 1.3—are so vital today.