Secure, Simplify, Innovate: Charting a Path to Adaptive Apps
Secure. Simplify. Innovate. Three simple words that describe every organization’s digital imperative.
Two years into the pandemic, it’s clear that we’ve reached a new baseline in the pace of digital adoption and transformation. Organizations of all types, sizes, and geographies increasingly view innovations in the customer and employee experience as necessary for survival. They are adopting new business models, processes, and technologies to better match today’s consumption patterns and enable safer delivery of goods and services.
This digital acceleration punctuates the set of opportunities and challenges that every organization is facing. Business leaders are making strategy and planning decisions to improve the customer experience, transform the business, and differentiate through their application portfolios. At the same time, IT operators wrestle with ever-growing security threats, legacy applications and infrastructures that still support the business’ most mission-critical activities, and crushing complexity.
So how do you successfully navigate this minefield of challenges and thrive in the digital future? Even to survive and maintain relevance, organizations must continuously make progress against these three interconnected objectives:
- Secure: Whether it be a software supply chain attack, rampant ransomware attacks, unpatched CVEs, or log4j vulnerabilities hiding in your apps, security threats are everywhere. And securing your most important assets—your applications—becomes increasingly difficult across hybrid, multi-cloud, or distributed cloud environments. Organizations must be empowered with robust application and API security capabilities that span on-premises, public cloud, and edge environments while enabling the management and enforcement of consistent security policies across complex deployments.
- Simplify: Bruce Schneier summed it up best in 1999 when he said, “Complexity is the worst enemy of security.” Today, organizations have more than just their on-premises infrastructure to worry about. Now they have multiple clouds, edge environments, corporate and personal devices that require access to sensitive data—a growing mix of application architectures ranging from monolithic, to microservices, to mobile, and everything in between. The keys to taming this complexity are standardizing on cloud-agnostic application security and delivery solutions, operating cloud-agnostic infrastructure where possible, and consolidating and simplifying your solution portfolio.
- Innovate: Like security, innovation is table stakes for surviving, but it’s not sufficient for thriving in this time of digital acceleration. And, also like security, complexity is a terrible enemy of innovation. Complexity robs developers of their time and focus and increases operational cost and risk. F5’s playbook for secure innovation at scale represents best practices from leading innovators and empowers developers by establishing four principles: shift security left, embrace open source, treat infrastructure as code, and automate through self-service.
To help our customers achieve these objectives, F5 has sharpened our vision for adaptive applications. Following a year of gathering customer feedback, we’ve developed a more concrete value proposition we’re committed to delivering on and a roadmap of milestones our customers can look forward to as we advance toward that vision.
The Why of Adaptive Apps
Let’s start with the why: Why should organizations care about realizing this vision of adaptive apps? Adaptive apps mitigate critical business challenges by delivering benefits that align to our customers’ most important priorities:
1. More rapidly detect and neutralize security threats. Customers can minimize the time it takes to detect and address threats based on a comprehensive understanding of the security posture of their application estate and real-time analysis based on ML techniques against the evolving threat landscape. Better yet, customers can rapidly eliminate the threats themselves via guided remediations or even automatic mitigations powered by advanced analytics and automation toolchains.
2. Improve application performance and resilience. Customers can execute policy-driven actions that prevent performance degradations and application outages by leveraging rich application telemetry and analyzing the data across time and peer applications. In addition, customers can reduce the number of critical incidents and improve their critical incident response time via rapid and well-informed adjustments to the infrastructure, leveraging robust troubleshooting tools, insights from application behavior, and effective automation.
3. Speed deployment of new apps. Customers can lower costs and deploy and maintain applications faster by pairing automation with insights and advanced deployment techniques, such as dynamic, behavior-based WAF rules and A/B testing of deployment configurations.
4. Easily unify policy across on-prem, public cloud, and edge environments. Customers can unify policy declaration and enforcement by defining and managing application security and delivery policies through a single management console. In addition, they can use built-in automation capabilities to enforce those policies across legacy and modern apps that span on-prem, public cloud, and edge environments. This ultimately enables customers to reduce the cost and complexity of operating apps across disparate application environments.
Aligned with these benefits, F5’s 2025 vision is to enable our customers to reduce manually handled threats, improve application performance and resilience, reduce the time to deploy new apps, and reduce the cost to implement app security and delivery policies across on-prem, public cloud, and edge, all by orders of magnitude, across their modern and legacy applications.
The What of Adaptive Apps
Now that you’re armed with the why, it’s more straightforward to understand the what. In summary, adaptive applications bring intelligence and real-time changes to application deployments, which today are mostly static and manual. Adaptive apps utilize an architectural approach that facilitates rapid and fully-automated responses to variables of consequence—for example, new cyberattacks, updates to security posture, application performance degradations, or rapidly changing conditions across one or more infrastructure environments. These apps are enabled by the collection and analysis of live application and security telemetry, orchestration of dynamic service management policies, and robust automation toolchains.
Let me be clear: simply running apps in the public cloud or developing new apps in a container-native, microservice architecture is not sufficient to realize the full value of adaptive applications. At the same time, an application doesn’t have to be based on a modern architecture to be adaptive; you can also make legacy applications more adaptive without refactoring.
Take, for example, a large financial services company whose online banking app recently suffered an outage. When one of its most popular, integrated, customer-facing services went down, concerned end users rushed to check their online accounts. The run on the online app caused demand spikes that couldn’t be handled by the brittle application delivery architecture that relied solely on hardware solutions already running precariously near capacity. A more resilient, more adaptive architecture augments modern hardware with scale-out software and isolates fault domains with a per-app model for application security and delivery.
The How of Adaptive Apps
We aren’t starting from ground zero in delivering the benefits described above. Today, we have multiple customer case studies and references that demonstrate how we’re already delivering real customer value for each of these benefit areas. And, going forward, we’ve established a roadmap of customer value milestones to deliver greater ROI on the way to our 2025 commitment. These customer value milestones are guiding our product investment and roadmap decisions across the F5 portfolio.
To illustrate, in terms of reducing manually handled threats, many F5 customers are already using our solutions to identify good and bad application traffic and to attach a powerful signature-based WAF to any app. Going forward, customers can expect expanded capabilities in 2022, 2023, and 2024 that enable them to detect and stop more malicious attacks and remediate environments with greater levels of automation, all while extending granular security controls to their microservices and APIs. Similarly, we have concrete proof points and a roadmap of customer value milestones established for each of the four adaptive apps benefits described above.
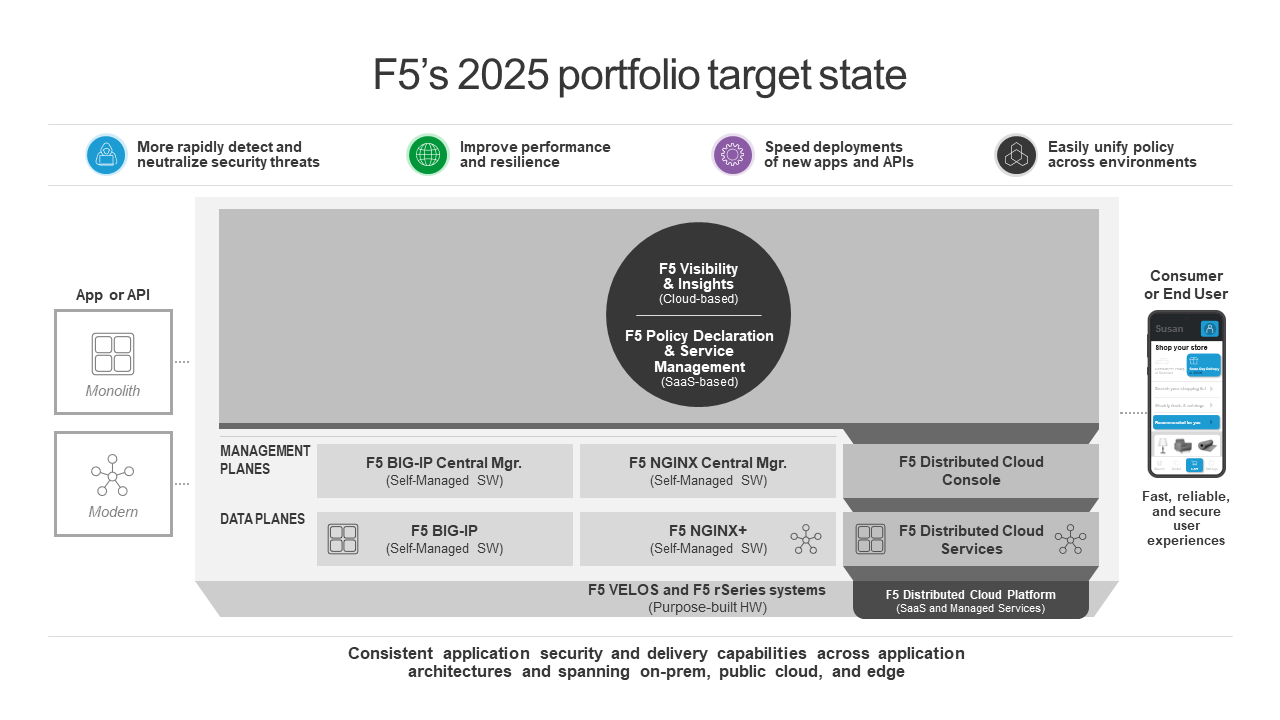
Our customers, along with investors, analysts, and others, have watched us acquire companies like NGINX, Shape, Volterra, and Threat Stack over the past three years. I know from spending time with our stakeholders that they are very curious about how we’ll bring these assets together with BIG-IP to help customers achieve their target business outcomes—so I’m proud to share how we plan to do just that by presenting F5’s tech stack for adaptive apps and our 2025 portfolio target state.
We’re hard at work executing our portfolio roadmap to get us there, including:
- Building a best-in-class portfolio of application security and delivery SaaS offerings, delivered on a common platform for SaaS and managed services. We are making it easier to build security into every application.
- Using telemetry and analytics to generate actionable insights and drive close-looped automation. Our approach offers customers multiple tiers of telemetry aggregation and analysis, as well as the flexibility to leverage F5’s management, analytics, and visibility tools or use their own.
- Simplifying automation and ecosystem integrations via common APIs that are shared across product families and layers of the stack and are also versioned and declarative.
- Unifying our product families to reduce complexity and offer a more seamless customer experience, including the buying experience, product telemetry standards, a single cloud-based data pipeline and analytics engine, a common SaaS capability for policy declaration and service management, and common UI components and design.
Starting Your Journey to Adaptive Apps
We realize the world of adaptive applications won’t happen overnight. But it’s also not a world well beyond reach in some distant, unattainable future. As with the customers we recently highlighted at Agility 2022, realizing the power of adaptive applications is a journey that any organization can start today.
F5 will meet you where you are; you choose your starting point. Whether that’s simplifying your legacy app security and delivery, securing apps and APIs everywhere, or enabling modern apps at scale, together we’ll transform how we secure, simplify, and innovate to ultimately bring a better digital world to life.
By Kara Sprague, Executive Vice President and General Manager, App Delivery and Enterprise Product Ops