Redefining Cybersecurity at the Distributed Cloud Edge with AI and Real-time Telemetry
Changing Application Landscape Introduces New Attack Surfaces and New Security Risks
Digital transformation and adoption of cloud technologies are happening at a rapid pace. With digital transformation, applications have become the lifeblood of businesses. As enterprises adapt to the macro trends impacting us all and adopt an application modernization journey, application architectures are changing to be API-first, microservices-based, and heavily reliant on automation and orchestration.
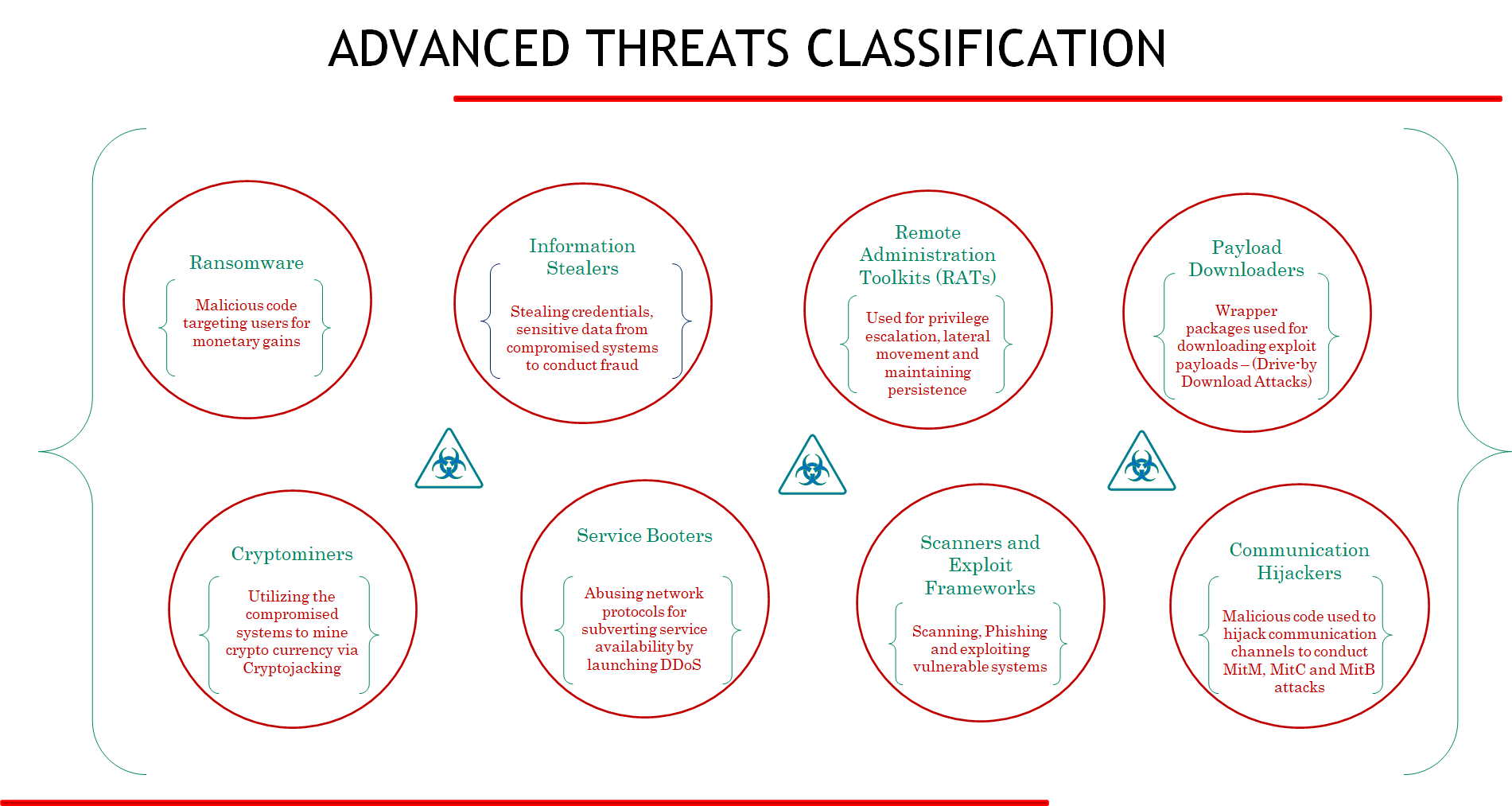
Attackers are taking advantage of this fast-changing application landscape with new attack methods to exploit the introduced attack surfaces. Unlike the previous security threats faced by enterprise customers, these new categories of attacks are highly organized and financially motivated. Attackers use specific tactics or intent to target specific assets. The picture below is a classification of some of the common advanced threats based on the ‘intent’ of the threat actors. We are very familiar with recent ransomware activities and there are several other prevalent threat activities, like the work of threat actor TeamTNT to compromise workloads in cloud environment.
AI-based Security is a Promise to Provide Security at Speed
These types of attacks typically bypass the well-established security controls, such as firewalls, web application firewalls, etc. Detection of such activities requires a very large amount of contextual information that can be corelated in near real time to determine the advanced threat activity in progress. In a nutshell, advanced threat activity detection is now becoming a big data problem!
Augmenting well-established security measures for web, application, firewall, and fraud mitigation techniques, F5 is researching techniques to detect such advanced threats, which require contextual analysis of several of these data points via large-scale telemetry, and with near real-time analysis. Machine learning and artificial intelligence algorithms are used to detect anomalous activity in and around applications, as well as cloud environments, to tackle the risks upfront. However, large data volume and rising customer expectations of fast performance collide. This is where NVIDIA BlueField-2 Data Processing Unit (DPU)-based real-time telemetry and NVIDIA GPU-powered Morpheus cybersecurity framework come into play.
Cybersecurity Poses Unique Requirements for AI/ML Processing:
- Due to fast-paced agile development and ephemeral workloads, there is an increased emphasis on unsupervised methods, such as clustering or anomaly detection over methods that require human supervision or labeling.
- The second important aspect is explainability. Part of this must be taken in the context of helping customers build trust in a solution, where a false positive or false negative may cause the loss of a customer, or more broadly, trigger an audit or compliance check. Empirically, a 90% effective solution that's explainable is often more attractive to a customer than a 95% solution that is inscrutable.
- The third and most important aspect is the ‘adversary effect’—that is, the fact there are well-funded, intelligent, active adversaries. Unlike, for example, vision recognition for autonomous vehicles where the set of street signs to recognize is static, security involves humans—perhaps even AI-assisted humans—that are analyzing and continuously trying to actively fool or circumvent your ML solution.
NVIDIA Morpheus Addresses New Cybersecurity Challenges
With the launch of the Morpheus cybersecurity framework, NVIDIA is bringing the power of AI data science to the cybersecurity industry. The highly optimized AI pipeline and pretrained AI capabilities of Morpheus allows developers to instantaneously inspect all IP traffic across the data center fabric.

NVIDIA BlueField-2 DPUs Accelerate Real-time Telemetry
Morpheus is a perfect solution for aggregating and analyzing real-time network data from any DPU-enhanced server. Meanwhile, BlueField DPUs offload, accelerate, and isolate mission-critical infrastructure functions. Morpheus receives massive amounts of network telemetry data from the agents running on the NVIDIA BlueField DPU and can perform real-time inferencing across this massive amount of data. Morpheus is then able to generate actions from raw inference results that are routed back to the DPU. The two-way stream of data to and from Morpheus and DPUs allows for continuous and real-time feedback to impact policies, rewrite rules, adjust sensing, and more.
Accelerated Inferencing Detects Cyberthreats Quickly and Efficiently
Morpheus provides real-time inference of large amounts of telemetry, thanks to the addition of GPUs into the workflow process. The GPUs process data through ingestion, into pre-processing, to inference, through post-processing, and offer parallelization to move a massive amount of data through the pipeline. By dividing the data and actions into manageable batches and executing them concurrently, Morpheus keeps up with data flowing from heterogeneous, decentralized/distributed, and mobile sources.
Morpheus uses Kafka, a publisher/subscriber model, to send data to and get results from the inference pipeline. The Morpheus framework is built using several building blocks including RAPIDS for data processing, Cyber Log Accelerators for GPU-accelerated open source cybersecurity primitives, Triton and TensorRT as inference servers, cuStreamz for accelerated Kafka reading and writing, and MLFlow, an open-source library to load new and updated AI models. These technologies work together to address all parts of the cybersecurity workflow.
By incorporating the Morpheus framework, F5 offers a powerful platform to accelerate web and API cybersecurity on every server through real-time telemetry and AI-powered analytics for applications distributed across the cloud and the edge.
Please join us at NVIDIA GTC to learn more about F5’s Shape cybersecurity portfolio accelerated with the NVIDIA Morpheus framework & BlueField DPUs. You can register here for free.

