Migrating Tier 1 Application Workloads to AWS with F5
Enterprises that are considering migrating or deploying production workloads in the public cloud are likely to consider Amazon Web Services (AWS) as their platform of choice. Today, AWS has more than 1 million active customers scattered across 190 countries, including 2,000 government agencies and 5,000 educational institutions.1 According to Gartner, AWS continues to be the overwhelming market share leader in terms of both revenue (47%)2 and share of application workloads (41.5%)2 deployed on public cloud Infrastructure-as-a-Service (IaaS). This paper reviews many of the factors that have inhibited broader adoption of the public cloud for enterprise applications and suggests how F5 application delivery services play a critical role in helping accelerate AWS adoption.
For most enterprises, applications are not static resources with clearly defined performance parameters; they must frequently adapt to unexpected spikes in demand to ensure user experience is not impacted. Due to the inflexibility of in-house IT services and the need to invest in fixed assets, IT organizations have traditionally responded to fluctuating demand by provisioning infrastructure and application resources to meet peak, rather than average demand. But procuring and deploying new infrastructure, networking, and the associated application resources is a complex and time-consuming process that requires considerable CapEx investment.
AWS partially solves this challenge by having already made the necessary investments in infrastructure and software assets, enabling enterprises to reap the benefits of unlimited capacity without overprovisioning resources. The advantages of using a public cloud IaaS provider like AWS is the agility it affords enterprises to rapidly deploy new applications, the flexibility it provides to allocate resources on demand, and the economics of an OpEx versus CapEx model.
It should be no surprise that application security, performance, and management control are among IT’s top concerns when considering moving applications to the cloud. While AWS provides many native tools and services to address some of these application delivery factors, those tools have varying capabilities and feature sets that might not meet application requirements.
Given today’s threat landscape, most organizations rank security as their number one concern for cloud-hosted applications. It’s critical to protect against the sophisticated malware and blended layer 4–7 security threats, such as volumetric DDoS combined with application layer attacks (OWASP Top 10, cross-site scripting, SQL injection, etc.) when moving workloads to any public cloud infrastructure. AWS uses a shared responsibility model with regard to security, which is divided into two segments; security of the cloud and security in the cloud. Security of the cloud relates to the security of the underlying IaaS infrastructure (compute, storage, physical hardware, etc.) – this is the responsibility of AWS. Security in the cloud is all about protecting everything above the hypervisor layer (OS, applications, data, etc.) – this is the consumer’s responsibility.
Consistent application access is also a requirement. How do organizations ensure access is uniform for all users, regardless of device or location, while also conforming to internal policies? Password fatigue can compromise security if users are tasked with memorizing multiple username/password combinations, which can lead to reduced efficiency. Most enterprises are likely to be deploying public cloud workloads in addition to workloads deployed in their own data center/private cloud environments. As such, it is essential for these users to be able to replicate and enforce consistent and proven security practices/policies across their hybrid cloud environments.
User experience and productivity continue to be important considerations, and both are dependent on applications performance in the cloud. In some cases, the cloud provider’s data center will be farther away from users, which means there will be increased latency between user and application, impacting performance. In addition, some of the methods that are typically used to deal with latency, such as caching, compression, and TCP optimizations, are not available in AWS.
Most enterprises require advanced traffic management (beyond basic load balancing) in their data centers for their business-critical applications. While AWS offers basic load balancing services via elastic load balancing (ELB) and application load balancer (ALB), organizations should consider what protocol support beyond HTTP/HTTPS and TCP is required. Will basic health checks and load-balancing algorithms be sufficient? Consumers often need to manipulate application data, which requires full L7 application proxy functions, such as URL inspection and rewriting. The ability to see incoming client traffic with context is critical to making granular traffic steering decisions.
Addressing the above concerns requires advanced and programmable application delivery and security services delivered through a unified platform like F5’s BIG-IP solution. This platform ensures the security, performance, and availability of all applications, regardless of their location. It also enables delivery and management of application services and their associated policies in a consistent way across all hybrid environments, for both new cloud-based applications, as well as existing applications.
F5 BIG-IP Virtual Editions (VEs) are virtual BIG-IP appliances that deliver the same, consistent set of services that are available across all BIG-IP hardware, including application and networking services—from intelligent traffic management (both local and global), acceleration, and optimization, to DNS, advanced application access, and sophisticated application security. These services can be fully integrated as part of the application stack and configured automatically. As the market leader in both hardware and virtual Application Delivery Controllers (ADC), and with 48 of the Fortune50 companies currently relying on F5 application services, it’s more than possible that F5 is already employed in a given business to service and protect applications.
BIG-IP VEs provide comprehensive L4–7 security services that protect cloud applications without requiring you to sacrifice control, flexibility, or visibility. These services complement AWS offerings and, through a sophisticated WAF (Web Application Firewall), complex DDoS attacks, web scraping, multilayer web-based application attacks, data theft, and leakage can all be prevented. With the intelligence and advanced behavioral analysis to recognize anomalous traffic patterns, F5 solutions can detect and mitigate automated botnet attacks. Leveraging the power of F5 iRules® data path scripting, F5 solutions can quickly respond to exploits of application vulnerabilities and zero-day attacks. With F5, the effort and expertise invested in tuning and configuring firewall rules and policies for each in-house application can be leveraged and reused by VE’s for cloud-hosted applications.
F5’s identity and access management architectures are based on full user, device, environment, application, and network contextual awareness. That means F5 solutions enable identity federation and single sign-on for application access across the data center and the cloud. At the same time, they enable the security of the applications and integrity of data with secure, context based access, protection from web-based malware and persistent threats, and comprehensive endpoint device inspections.
BIG-IP advanced local traffic management services support a broad range of protocols beyond HTTP/TCP (e.g., HTTP 2.0, SPDY, and UDP) and deep application fluency. As a full-proxy architecture, the BIG-IP platform provides complete visibility into application traffic, decrypting and re-encrypting SSL traffic in the process. It also dynamically tracks the performance levels of servers in a group and provides deep health monitoring and connection state management. BIG-IP application delivery optimization services can accelerate application response time, minimize latency and delays, and reduce the number of data round trips necessary to complete web requests from mobile devices.
BIG-IP DNS and global server load balancing services direct users to the nearest cloud data center that would deliver the best user experience, disaster recovery, and failover policies. User proximity, geolocation, network conditions, and application availability are all factored into routing decisions. The platform employs a range of global load balancing methods and intelligent monitoring specific to each application and user. F5 also offers DNS DDoS protection, blocks access to malicious IP addresses, and secures responses with DNSSEC. Best of all, DNS queries and health checks are not billed per use, avoiding the high cost of being charged for both legitimate and illegitimate queries during a DNS DDoS attack.
A key benefit in moving application workloads to public cloud platforms is the ability to scale an application beyond provisioned base capacity in the data center. With AWS Auto Scaling, applications maintain availability while automatically scaling Amazon EC2 capacity up or down according to pre-defined thresholds. BIG-IP solutions integrate with AWS Auto Scaling to enable dynamically scaled BIG-IP application and security services. And because BIG-IP VEs natively handle the addition or removal of pool members, there is no need for out-of-band orchestration and configuration management. In addition to the auto scaling of the BIG-IP LTM (see Figure 1.), F5 has released solutions that enable auto scaled application security, whereby both BIG-IP LTM and BIG-IP ASM are provisioned on the BIG-IP VE.
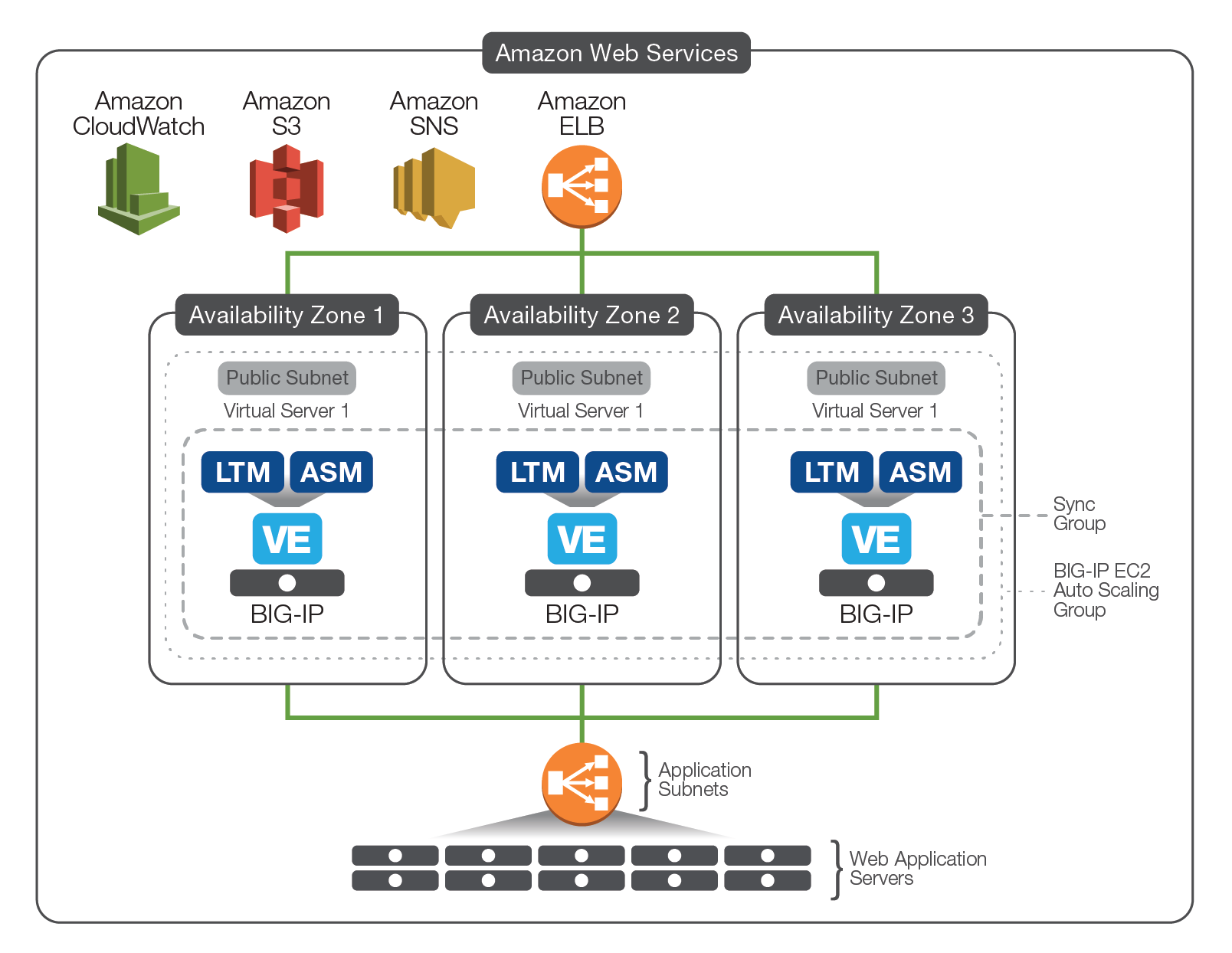
AWS Cloud Formation Templates (CFTs) provide a scripted method for automating the deployment of infrastructure (server, storage, networking, and compute) resources. They provide a repeatable way to rapidly deploy the same BIG-IP image and configuration multiple times within AWS, meaning precious working hours can be reallocated to more pressing business matters. Having been designed and tested extensively by F5 engineers, CFTs eliminate any worries associated with deploying or configuring the BIG-IP VE, ensuring F5 virtual appliances are provisioned with the confidence of an F5 expert. Not only that, but thanks the seamless integration with 3rd party automation tools such as Ansible, Chef, and Puppet, these CFTs simplify the process of automating and orchestrating BIG-IP VEs. All F5 CFTs are open-source and available free of charge through GitHub, allowing fellow F5 enthusiasts to change templates to better suit specific business requirements.
In addition, F5 has integrated more tightly with the AWS marketplace by making a selection of its CFTs directly available through the AWS Marketplace, for faster and easier implementation. For example, a variety of auto scaling solutions (auto scale BIG-IP LTM, auto scale WAF, etc.) can be selected for deployment from the marketplace and can be up and running in production environments in less than an hour, eliminating the need for F5 users to configure these complex solutions themselves—saving days, if not weeks, of working hours.
The DevCentral™ community site offers example configurations of VPC resources such as subnets, network interfaces, and routing tables for deployments of BIG-IP VEs. These examples also show how to use CloudInit user data scripts to deploy BIG-IP iApps® templates for specific packaged applications (Microsoft SharePoint, Exchange, and others) and custom applications. Similar in functionality to AWS CFTs, F5 iApps were created to help quickly deploy the specific services each application needs. iApps also defines the configuration and policies of services such as traffic management, encryption, firewall, and performance optimization for each application.
By integrating public cloud resources with an existing private data center, organizations can transition application workloads based on prioritized schedules while continuing to leverage existing investments. BIG-IP VEs, F5 iApps, and AWS CFTs work together to create an integrated cloud configuration that allows rapid and transparent deployment of additional application resources. Key advantages to this federated cloud configuration include the seamless redirection of application users, geolocation and acceleration technologies, and secure connections using AWS Direct Connect. The user experience remains unaffected whether application resources are delivered from a private data center or public cloud. Transparent and continuous use of private and public cloud resources can be based on demand, on whether a project is new or already in place, or on the specific location of the requester.
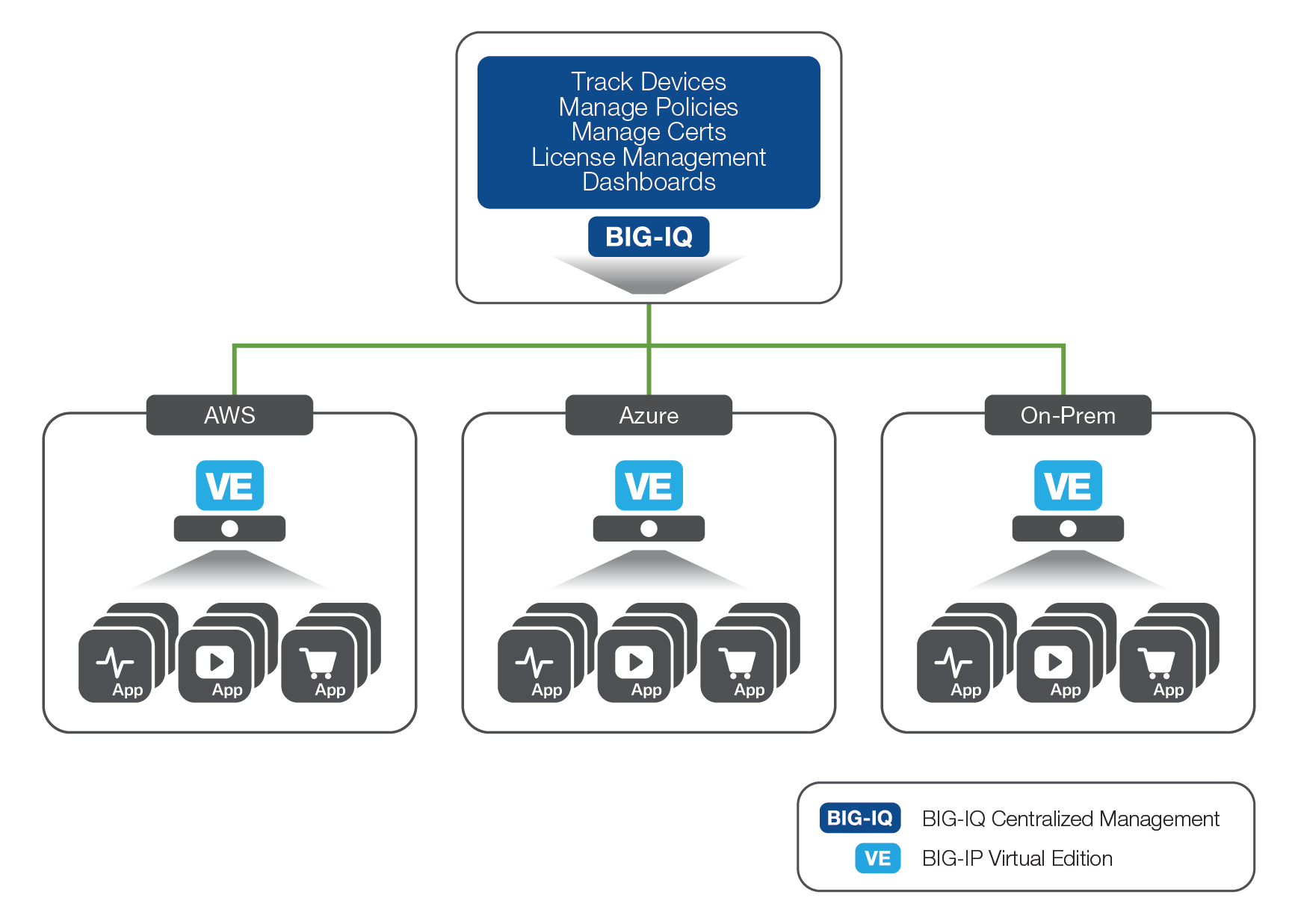
F5® BIG-IQ® Centralized Management provides a central point of control for F5 physical and virtual devices both in the cloud and on-prem. BIG-IQ Centralized Management simplifies application management, helps ensure compliance, and provides tools to manage F5 devices and services consistently and securely, wherever they reside. BIG-IQ Centralized Management handles policies, licenses, SSL certificates, images, and configurations for F5 devices and for the following F5 modules:
- BIG-IP® Local Traffic Manager™ (LTM)
- BIG-IP® Application Security Manager™ (ASM)
- BIG-IP® Advanced Firewall Manager™ (AFM)
- BIG-IP® Access Policy Manager® (APM)
- BIG-IP DNS (monitoring only)
- Dashboards for F5 Fraud Protection solutions WebSafe and MobileSafe
BIG-IQ Centralized Management is available as a physical or virtual appliance, or can be run directly from the AWS Marketplace.
BIG-IP Virtual Editions are primarily available in Good-Better-Best bundles, and in three distinct purchasing models:
- Utility billing. For test and development pre-production workloads, or temporary cloud bursting and scalability use cases, F5 offers hourly utility licensing that provides flexibility and on-demand, post-paid use. Premium support and software upgrades are included with all utility offers.
- Bring-your-own-license (BYOL). This option is ideal for hybrid cloud environments in which existing BIG-IP VE licenses are migrated from a private data center directly into AWS.
- Annual Subscription. In addition to perpetual VE Licenses, F5 also offers annual subscription BYOL VE licenses. They can be used across any supported hybrid cloud environment, providing greater portability and flexibility. Annual subscriptions are ideal for production workloads that have steady-state traffic and are available from the AWS Marketplace.
- Enterprise License Agreement (ELA). For larger enterprise environments seeking maximum flexibility and agility, ELA enables multiple VEs to be purchased in 3-year agreements, with premium support and software upgrades included.
Additionally, the BIG-IQ Centralized Management License Manager is available at no cost to manage BIG-IP product licenses across all hybrid environments.
Adoption of public cloud services has grown exponentially over the past few years, and AWS has been the consistent market leader for these services. Many IT startups, as well as larger, more well-known enterprises, have deployed entirely in the AWS cloud with significant success. As enterprises plan to migrate applications to the cloud, F5 application delivery and security services can be easily ported to cloud application workloads using F5 BIG-IP virtual editions. Doing so addresses many of the fundamental concerns that enterprise customers have regarding security, performance, and control in the public cloud. With flexible licensing models available for BIG-IP solutions in the AWS Marketplace, enterprises can plan, stage, and deploy applications in AWS with minimal financial exposure and begin to benefit from the agility and efficiencies of AWS cloud.