Infrastructure is still an attractive attack vector
Do you save a seat at the digital transformation table for your CISO? You should.
Several trends are driving infrastructure underground. Mainstream adoption of automation and infrastructure as code approaches to managing the foundation for applications have obfuscated the importance of the myriad network and application technologies required to deliver and secure applications.
Developers don’t want to be bothered with the nuts and bolts of infrastructure, particularly as it relates to networking. Cloud computing has long sought to remove the need to deal with infrastructure, laying on APIs and drag-and-drop configuration tools to help the network and infrastructure-averse avoid getting their hands dirty. Kubernetes, created by developers for developers, craftily kicks networking and infrastructure to the curb by hiding it beneath a layer of configuration and orchestration magic.
But that doesn’t mean we should ignore the existence of infrastructure or its profile as a key attack target.
To wit, three of the top ten vulnerabilities tracked by IBM X-Force in 2020 were infrastructure-related vulnerabilities.
I’ll wait while you digest that.
Filling out the top ten were application platform and framework vulnerabilities, as you’d no doubt expect. But three of them—including the top exploited vulnerability—targeted infrastructure.
For as long as there is a need for infrastructure—and that means the foreseeable future—there will exist a need to protect it. Infrastructure is the first point of contact in most architectures, with firewalls and DNS and load balancers taking the lead. These are critical infrastructure that can, when attacked, bring down the entire digital presence of an organization. Indeed, Cisco’s Annual Internet Report notes, “Infrastructure outages also continue to be a threat with over half of operators experiencing this issue.”
The relationship between infrastructure and business remains lukewarm. To be fair, business leaders place an almost equal importance on protecting infrastructure as they do the business and applications. Which is to say they are lukewarm about protecting, well, everything.
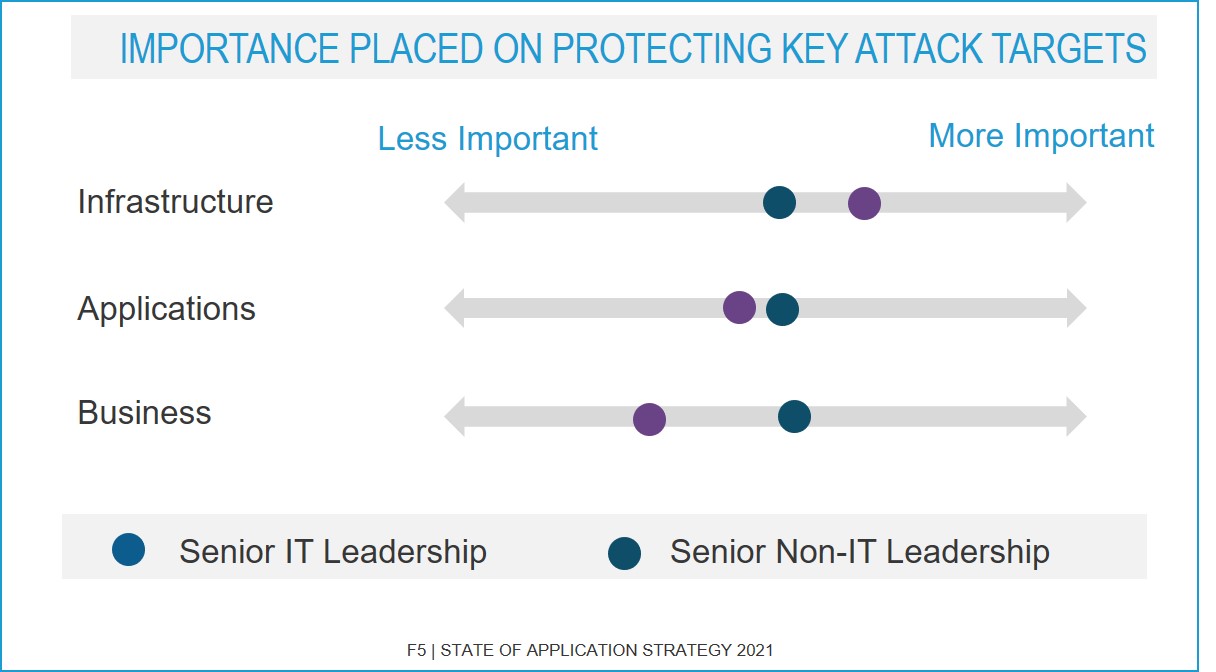
We chose these categories with a very specific reason in mind: together they form the digital business "stack." Digital business relies on applications, and applications rely on infrastructure. The three are inseparable in today's default-digital world, and yet they are obviously viewed as distinct things to be protected—or not—based on our perceptions of their importance by role in the organization.
The disconnect we see evident in the importance placed on protecting key attack targets indicates that most organizations are still maturing in their digital transformation journey. Business and IT need to come together as equal partners to efficiently operate and protect digital business. That means IT needs to view protecting the business as important as infrastructure—and vice versa.
While the digital transformation journey was certainly accelerated by COVID-19 and a rush to "go digital," maturity of practice and perceptions will take time to catch up. Today, PWC reports that as a result of COVID-19, over half of businesses are "more likely now to consider cybersecurity in every business decision—that’s up from 25% in our survey last year."
That’s a good start.
One of the ways forward for organizations who haven't yet adopted this practice is to look at who is sitting at the digital transformation table. While we often talk in terms of the CIO needing a dedicated seat, we are less likely to mention the criticality of inviting the CISO to the table.
The role of the CISO has shifted over time, sometimes abruptly. At its core, the role requires a focus on security. As business has embraced digital as default, that role has expanded to a more strategic one, a role that is as much about operating securely as it is about operating at speed. That means CISOs need to be involved in digital transformation from the beginning with the goal of putting place the policies and guardrails necessary for the organization to protect customer and corporate data while enabling acceleration of digital business.
If your CISO is not already a part of the digital transformation conversation, they need to be. Infrastructure is still a critical component of digital business, and it's still an attractive attack vector—and protecting infrastructure is still a responsibility of the CISO.
