How Online Accounts Get Taken Over by Cybercriminals
A friend recently shared a story of a game she played with her family as a child. While on road trips, they would try to guess where the people in other cars were from. Their guesses were based on limited information—at best the state on a license plate or bumper stickers.
Today, by contrast, our personal information is extremely easy to find across our digital assets, and it has become easier for bad actors to access them through social engineering tactics like phishing and smishing.
The psychology of a cybercriminal
Cybercrime, like most crime, starts with a notion of MOM—that is, Means, Opportunity, and Motive. It is important to understand the psychology of a cybercriminal and what drives them to commit cyber fraud:
- Means: The ability, tools, and means to commit crime are abundant. Now, more than ever, criminals don’t need to be sophisticated experts to commit fraud, thanks to a surplus of free tools and services they can use.
- Opportunity: There are plenty of potential targets. The booming application economy, with everything becoming digitized from money to personal healthcare records, means that cybercriminals have enough chances and targets to commit fraud.
- Motive: Usually, but not always, the motive is financial.
Assume you are under attack
In general, assume that every consumer-facing application and digital account you control will be attacked sooner or later. It happens to even the best-protected accounts because attackers have become skilled at abusing app logic to commit fraud.
Winning against cybercriminals demands teamwork. The team includes individual account holders and institutions’ application developers, fraud teams, and security teams. The right approach also requires a collective effort by individuals who use these applications and the companies that build them, and should start with security and fraud teams converging their defenses against automated application threats to stop bot attacks upstream which will prevent fraud downstream.
Bots are a double-edged sword
Automation, in and of itself, is a good thing. Bots automate repetitive tasks, help companies engage customers, and build brand affinity. For example, you may have interacted with a customer service chatbot to receive real-time responses to questions you had.
However, in the wrong hands, bots and automation are powerful tools that can be used to carry out malicious attacks such as credential stuffing for taking over accounts and committing fraud.
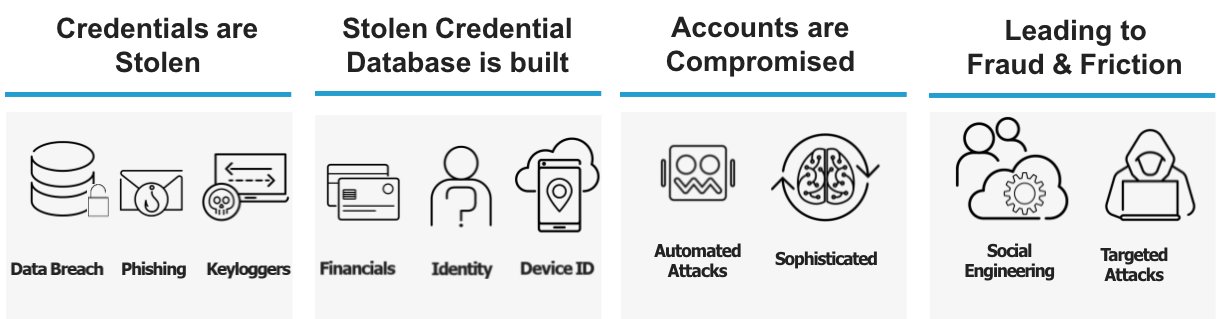
Typically, credential stuffing attacks leverage previously stolen credentials and test them across numerous domains. These attacks take advantage of the fact that usernames and passwords are commonly reused across many applications.
In fact, a recent report shows that employees will reuse passwords 13 times on average. Furthermore, even when consumers are notified that their accounts have been breached, only about a third change their passwords.
Cybercriminals capitalize on these weaknesses to commit many types of fraud, including:
- Financial fraud: Attackers use stolen personal information to open or access an account in the victim’s name to steal their money. These accounts may also support other criminal activities such as money laundering.
- Retail fraud: Attackers use stolen personal information to make purchases at retail stores or on e-commerce sites, hoard inventory, and steal gift cards that have a positive balance.
- Hospitality fraud: This type of fraud typically targets travel and customer loyalty programs. Attackers use fraudulent travel or hospitality services to harvest your credentials and identity information for other uses. They also use previously harvested loyalty points, air miles, and reward points for the purpose of booking travel services for themselves or others.
The problem of credential attacks
Identity-based credential attacks are the #1 source of automated web attacks that lead to fraud. Identity information is readily available to purchase in cybercrime forums. Lists can be found and purchased on some social media platforms.
Fresh credentials—such as those stolen within the past one to two days—are more valuable and cost more for cybercriminals to buy. Stale credentials are less valuable because their chance of success is much lower. Since valuable credentials and personal identifiable information are obtained from external account breaches, these attacks are difficult to identify and stop.
Let's walk through an example. Once credentials are stolen or acquired, cybercriminals use bots or other automated tools to attempt to create or access accounts. Thousands (or even millions) of attempts may be made. The success rate of credentials-based attacks hovers between 0.2%-2%. While these percentages may seem small, credential attacks do not need a high success rate because billions of credentials are available for free or at nominal cost.
Imagine hitting one million accounts and yielding a success rate of between 2,000 and 20,000. That is a staggering number!
Preventing account takeover and fraud
It is important to understand that each of these criminal endeavors are links in a chain of events. ‘The Industrialized Attack Cycle’ (see figure below) illustrates critical elements in the ecosystem. Unfortunately, this is a large, resilient ecosystem, so it is imperative for individuals and organizations to be vigilant in protecting themselves, their customers, and their business partners.
As individuals, we need to learn to identify potentially damaging phishing attacks, use extraordinarily strong passwords, and limit reuse of passwords across different accounts.
At the same time, security and fraud teams need to work together to collectively thwart the industrialized attack lifecycle.
Watch the video below to learn how F5 helps organizations protect themselves against cyber fraud.
Stay tuned for the final blog post in our four-part series for Cybersecurity Awareness Month that explores APIs and why they can be a security issue. Also, be sure to read our previous blog posts, How Modern Apps Are Built and Deployed and How Bad Actors Exploit Applications with Attacks.