Gaining Visibility into your Applications Requires Breaking Down Operational Silos
I’m now on my fifth week of working from home to #stopthespread of COVID-19. Each day reveals new tragedy and brings fresh grief as the humanitarian crisis unfolds. Each day, I’m also inspired by the dedication, professionalism, and altruism of those fighting the virus on the front lines in hospitals, clinics, and care facilities as well as those working to keep essential services available. My heartfelt thanks go out to those heroes.
This crisis has also brought out heroes in IT departments in organizations around the world. Our reliance on digital services has significantly increased in the past month and so too has the commitment, ingenuity, and hard work of individuals from teams across network operations, DevOps, security, and development to scale these services effectively and securely. They are putting in long hours in less than ideal circumstances to ensure smooth operation of everything from keeping remote workers connected, to delivery apps bringing essential items to our door, to telemedicine solutions activating large armies of trained health professionals.
Some market analysts have estimated this work could advance companies’ digital strategies by up to a decade. They will, however, need to tackle a number of challenges to get there. In my last blog, I discussed the most significant of these challenges: a lack of visibility into their applications.
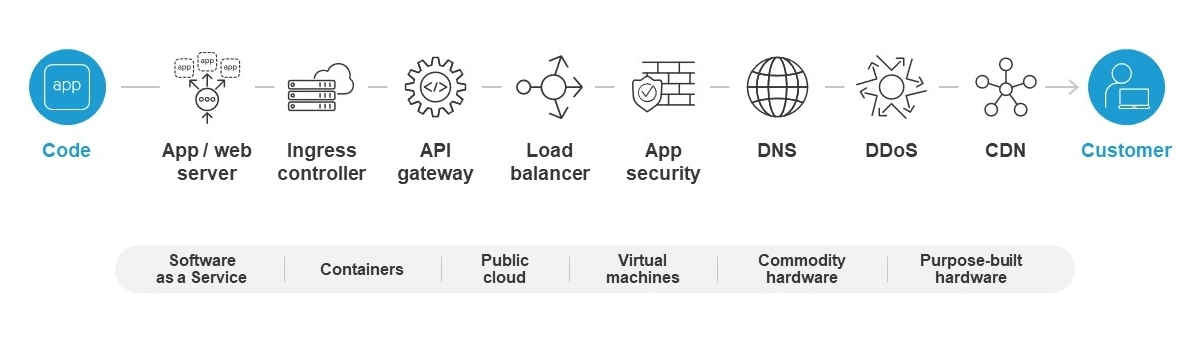
One of the reasons why application-level visibility remains so elusive is because application data paths are complex and have not generally been constructed for end-to-end visibility. An application data path is the pathway through which the traffic of an application flows, from the server on which the application business logic is hosted, to the end user trying to access the application. Most applications have several technologies or services along the data path. Depending on how you count them, there are at least seven to nine of these different services along the data path for a modern application, spanning everything from the runtime environment to the edge delivery network.
Each of these services along the application data path could be served by any of several vendors. And for each different application architecture (e.g., monolithic, client-server, 3-tier, microservices, mobile) and each infrastructure environment (e.g., on premises, Amazon Web Services, Microsoft Azure, RedHat OpenShift, Pivotal Cloud Foundry, etc.), there are more vendors. The vendors and tools our customers select for their monolithic and 3-tier applications are generally not the ones serving their microservices applications. And they often have a different toolchain entirely for their various public cloud application data paths.
That’s a lot of vendors—and a lot of tools.
Most of our customers have structured themselves internally around all those vendors and tools, too. Historically, this made sense because each role and each tool often requires its own knowledge base, skillsets, and processes to manage. The team managing the Azure applications is often separate from the one managing the AWS applications, which is separate from the team responsible for the legacy on-premises applications. The same is true with the various disciplines and roles involved. The App Developers, the SecOps teams, the NetOps teams, etc., each use toolsets most relevant to their specific jobs in delivering and securing each application.
Each of those tools and vendors along the application data path usually comes with its own central management and automation framework. This leaves the work of stitching everything together to the customer. To add some dimension to this, F5 research finds that enterprises have an average of ~800 applications in their portfolio, spanning ~4 application architectures and ~3 infrastructure environments (i.e., on-premises and 2+ public clouds). Furthermore, each of those applications has seven to nine services along the data path. It’s no easy feat to automate and orchestrate a single application data path, let alone solve for a typical enterprise’s heterogenous portfolio.
What ultimately results from all this—what we’ve all gotten ourselves into—are silos. There are several operational silos along the data path for a single application, and even more operational silos for each of the application architectures and infrastructure environments used within any multi-cloud architecture.
And where there are silos, there is limited visibility. When something goes wrong along the application data path, it can sometimes take weeks or months to figure out exactly what happened. Never mind tuning for optimal end-to-end performance when things are going well.
And that is the state that most of our customers finds themselves now. On the one hand, they have sprawling application portfolios spanning traditional apps that are critical to keeping the business operating today and modern apps that are core to their value creation going forward. And on the other hand, they have an immature operational model for that application portfolio that is hardened around organizational siloes and fragmented tooling, thereby perpetuating the existence of tremendous blind spots and risk.
To help our customers realize and secure the full value of their applications, F5 advocates for a new paradigm for application delivery and application security that is fundamentally oriented around the application. In contrast to the traditional paradigm that optimizes around a subset of the application data path capabilities and extends down into the infrastructure layer (we call this the “vertically-integrated approach”), this new approach focuses on streamlining the end-to-end application data path and abstracting that layer from the underlying infrastructure. There are several benefits to this approach:
- Achieve application portability and avoid infrastructure lock-in
- Gain end-to-end visibility for improved application availability and security
- Orchestrate and automate application delivery for amazing experiences in a consistent way across the entire application portfolio, regardless of application architecture or infrastructure
There are several reasons why F5 is ideally suited to deliver on this promise to our customers. First, between F5 BIG-IP, NGINX, F5 Cloud Services, Silverline, and now Shape, F5 has the most comprehensive set of capabilities along the application data path—web servers, Ingress controllers, load balancers, and application security—of any solution provider in the world. And we offer those capabilities in a variety of consumption and deployment models.
We also have the only truly multi-cloud (i.e., platform-independent) set of data path elements. This means that you can run F5 data path elements (we call them “application services”) anywhere. You can run them in container environments—in fact, NGINX is specifically optimized for container-native environments. Our application services run in the public cloud. They also run on virtual machines, on commercial off-the-shelf hardware, and on our own purpose-built hardware.
And between our existing ecosystem integrations and the world-class declarative APIs that enable our customers and partners to integrate and orchestrate F5 technologies with third-party technology, we also offer the most open architecture of any solution provider. That gives our customers choice. They get to choose which best-of-breed technologies they want to use along the application data path and elsewhere.
And now, with NGINX Controller and F5 Beacon, we’re offering packaged solutions to help stitch it all together in a way that doesn’t just allow the technologies to interoperate, but that also enables all those human groups to collaborate.
Our long-term vision is to expand on these powerful services and deliver more insights via telemetry and analytics. And from there, we’ll focus on turning these insights into tangible top-line business value for our customers across all industries—something we refer to as AI-Assisted Business.
We’re already seeing customers achieve impressive results as we begin to deliver on this vision, and we’ll be sharing more about those results and about the next steps we’re taking in the weeks and months to come.