F5 SSL Orchestrator Further Benefits Customers Thanks to Strong Partnerships
As F5 readies a new release of our hardworking SSL Orchestrator (SSLO) product, it is again time to call attention to the important role that partnerships play in customer security. At F5, we partner with many of the world’s leading security companies to create an ecosystem that strengthens security, increases scale and availability, and reduces operational costs. The ultimate goal of these close collaborations is to foster integration and interoperability that benefits you, our joint customers; and SSLO is a model example of this interoperability in action.
Before I discuss F5 SSL Orchestrator integration with our partners’ solutions, let’s first have a quick refresher on what this product does.
Don’t let SSL/TLS blind you to threats
When we talk about SSL, we’re basically talking about encryption. And the tricky thing about encryption is that it takes a lot of resources to accomplish all the de-encryption and re-encryption that is required in order to inspect it for bad stuff. “Bad stuff” in this case is the highly technical term for the likes of DDoS attacks, [zero-day] web exploits, droppers [binaries], and multi-protocol callbacks, to name a few.
F5 SSL Orchestrator is our answer to addressing blind spots created by encryption. This versatile software solution, available on a range of F5 platforms, is designed specifically to optimize your SSL infrastructure by providing security devices with highly efficient visibility of SSL/TLS encrypted traffic. We also support policy-based management and steering of traffic to existing security devices, which is what makes it so easy to integrate into existing architectures—and other vendors’ solutions—enabling you to easily apply corporate security controls to all your encrypted traffic.
Dynamic Service Chaining—Decrypt once, inspect often, re-encrypt once
To solve specific security challenges, IT administrators typically will chain together multiple point-products to create a comprehensive security stack. A stack might include, for example, data loss prevention (DLP) scanners, web application firewalls (WAF), web proxy, intrusion prevention systems (IPS), malware analysis tools, and so on. SSL Orchestrator eases the creation and maintenance of such chains by determining whether traffic should bypass or be decrypted and sent to one service or another. Using policies to automate traffic steering like this reduces administrative costs and enables you to gain more value from investments already made in security services.
Our partnership with FireEye® is one example of where SSLO service chaining brings you value. Traditionally, an intrusion prevention system (IPS) such as FireEye Network Security would be deployed inline and all traffic would flow through it—which means it also had to be sized to handle encrypted traffic, even though that traffic could not actually be inspected (precisely because it was encrypted). The modern solution is much more efficient. By utilizing SSL Orchestrator, we are able to send the IPS only the traffic that needs to be inspected.
“The FireEye integration with F5’s SSL Orchestrator enables the FireEye Network Security offering to extend its capabilities to include additional forms of data and provide extended use cases,” says Rich Stegina, VP of Strategic Technology Partners at FireEye. “The performance of FireEye Security solutions is enhanced when freed of the burden of content de-encryption and encryption. In such circumstances, our clients can achieve increased visibility into potential security threats.”
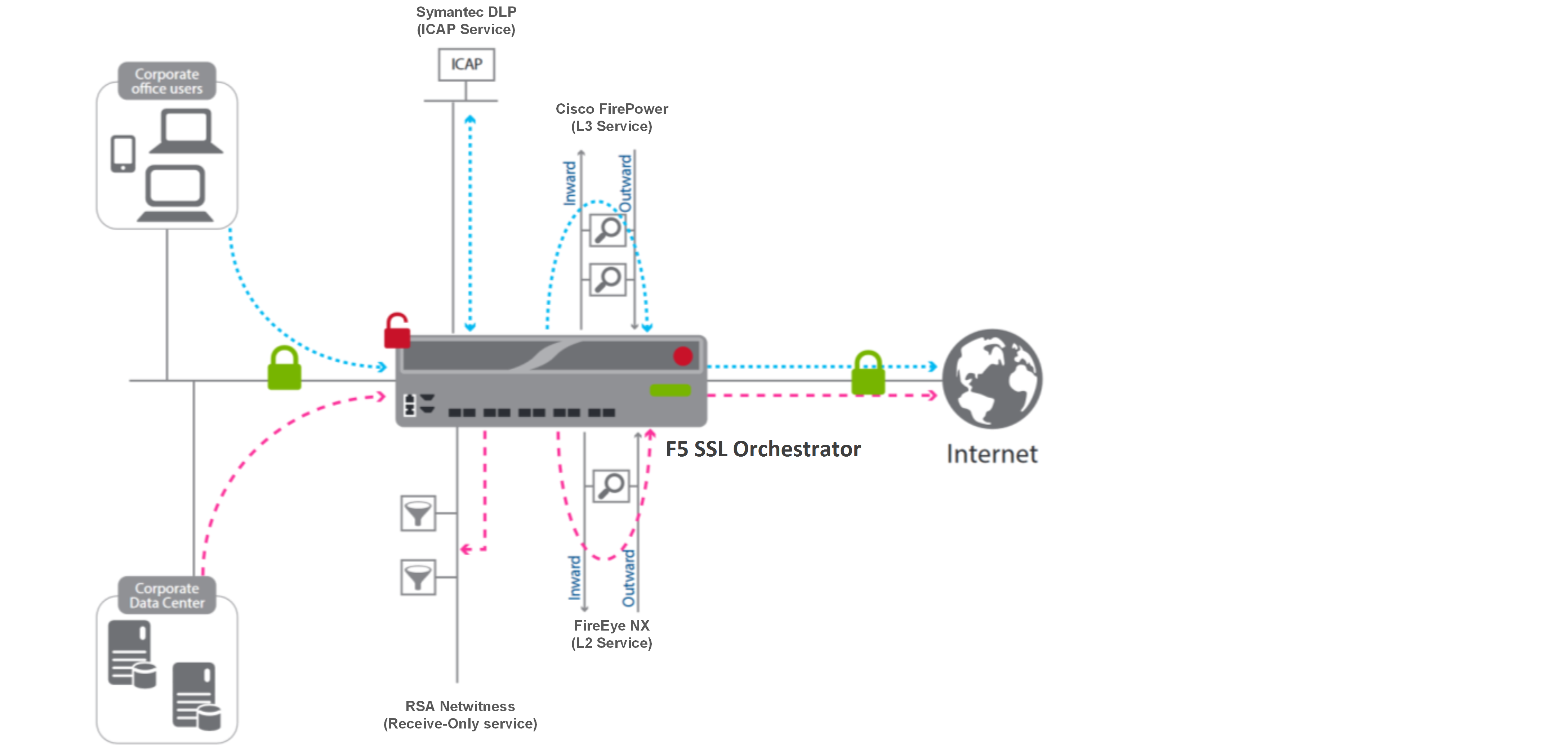
Next-gen firewalls are another great example of a network device that benefits from SSL Orchestrator. The leading Cisco Firepower NGFW, for example, is a fully integrated, threat-focused next-gen firewall and next-gen Intrusion Prevention System with unified management. It uniquely provides advanced threat protection before, during, and after attacks.
And as before, when Cisco Firepower NGFW is a part of your SSLO service chain, F5 centralizes SSL decryption/re-encryption with best-in-class SSL hardware acceleration, thereby removing that processing burden on every security inspection hop in the stack. With decryption/re-encryption out of the way, your Cisco Firepower NGFW can focus on what it does best.
“Cisco Firepower NGFW performs an impressive array of tasks on an incredible amount of traffic,” says Douglas Hurd, Technical Alliance Manager at Cisco, “and while customers can use onboard SSL decryption to gain visibility, many choose to offload this computationally intensive work with F5 SSL Orchestrator, which means we can devote more of our horsepower where it counts—protecting our customers.”
Many other partners benefit from having an SSL Orchestrator upstream of their product or solution. Symantec DLP tools are another good example, as are RSA NetWitness Suite and Palo Alto Networks’ Next-Gen Firewall. Really, any service that inspects traffic will benefit from SSL Orchestrator’s ability to pass-through only relevant, actionable data. And the benefits are clear:
- Better traffic management means your security infrastructure and, hence, your applications run smoothly.
- Service chaining delivers the benefit of having to decrypt traffic only once, allowing for multiple inspection points, and then re-encrypting the traffic once.
- Intelligent orchestration of decrypted traffic in the security stack, breaking the daisy-chain paradigm, and allowing devices to be independently addressed, load balanced, monitored, failed around, and ultimately scalable irrespective of other security devices.
- Advanced decryption capabilities ensure that threats don’t hide within encrypted traffic.
More developments to come
Stay tuned for exciting new SSL Orchestrator capabilities coming later this year. SSLO delivers critical functionality to such a wide range of devices and solutions, it is quickly becoming one of our marquee products, and we’re working hard to ensure it continues to deliver value—both to our partners and our customers.
