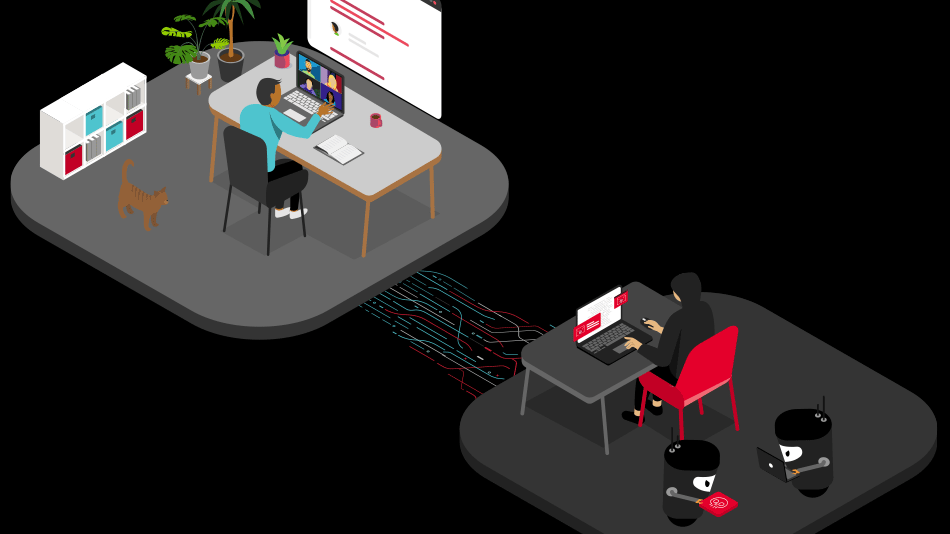
What is a Credential Stuffing Attack?
Credential stuffing is a type of cyberattack where an attacker attempts to gain unauthorized access to a protected account by using compromised credentials.
Credential stuffing abuses digital interfaces and workflows such as login forms to gain unauthorized access to customer accounts. These attacks typically leverage automated tools and compromised credentials, but often evolve to imitate human behavior or impersonate real customers.
Commonly used mitigations to combat credential stuffing, including CAPTCHA and multi-factor authentication (MFA), are easily bypassed by sophisticated attackers and can frustrate real customers, leading to abandoned transactions and lost revenue. Additionally, credential stuffing is often the precursor to account takeover (ATO) and fraud.
Credential stuffing has emerged as a top cybersecurity problem in the world. In 2018 and 2019, the combined threats of phishing and credential stuffing made up roughly half of all publicly disclosed breaches in the United States.1
This attack is popular because of the high ROI—success rates typically hover between 0.2 and 2%.2
The median time to detect credential compromise is 120 days, and they are often on the dark web prior to disclosure.
Attacks are constant due to the frequency of data breaches, success of phishing, and fast monetization of credentials using automation. This creates a vicious circle in which organizations suffer intrusions in pursuit of credentials and credential stuffing in pursuit of profits.
Credential stuffing starts with automation and compromised credentials and ends with account takeover, fraud, and customer friction.
Readily available tools, infrastructure, and billions of compromised credentials results in low attack investment and attractive hacker economics.
Sophisticated tools can emulate human behavior to bypass security controls and leverage human click-farms to evade anti-automation algorithms. These tools have further evolved to use AI models to bypass risk-based authentication.
Traditional migitations are ineffective at detering sophisticated credential stuffing and can insert friction into the digital experience, frustrating customers and constraining top line revenue potential.
F5 solutions deter credential stuffing attacks by disrupting their ROI—making success impractical or unfeasible.
By curating and analyzing network, device, and environmental telemetry signals across data centers, clouds, and architectures, F5 solutions can uniquely detect anomalous behavior and automated attacks that use compromised credentials.
Additionally, F5 solutions perform real-time obfuscation to neutralize reconnaissance and profiling by motivated adversaries, and maintain resilience and efficacy when attackers retool to bypass security countermeasures.
By modeling threat intelligence across similar attack profiles and risk surfaces, and leveraging supervised and unsupervised deep learning methods to detect attacker techniques, F5 solutions autonomously deploy appropriate countermeasures with maximum effectiveness.
This future proofs defenses against attacker AI models that attempt to bypass risk-based authentication, and prevents the ripple effects of account takeover and fraud across the business—from losses to missed revenue opportunities to damaged trust that can cripple operations and put the business at a competitive disadvantage.