Consistently Control Access to Multi-Cloud Applications with F5 Access Manager and Equinix
The issue of remote access has become a priority as our response to the pandemic continues to encourage, if not require, working from "anywhere but the office." The first wave of remote access concerns was focused on users. How do they access their desktops? Their productivity applications? Their business applications? Files? Databases? Code repositories? Many of these concerns are answered by a move to SaaS. This has always been likely given that generalized (commoditized) business applications were rapidly being served via SaaS anyway.
The second wave of remote access concerns is less visible but no less a priority: that of operational access to the dashboards and consoles IT relies on to deploy and operate infrastructure and application services. Because while there are some operations that require physical presence—addressing a failed hard drive implies the ability to physically remove and replace it—many do not. The infrastructure and applications that can be remotely addressed, should be.
Both are particularly tricky to manage, especially across multiple cloud and data center properties. Too often organizations, particularly those rushed into migration, can wind up with multiple access control points. One for Azure, one for Amazon, one for the data center, and so on. Setting aside the excessive operational overhead incurred by such a situation, one must consider the impact of multiple and discrete access policies across these domains.
First, because today’s infrastructure and applications are distributed combinations of automated components from multiple sources or vendors—deployed in central or regional colocation data centers, via cloud service infrastructures, across multi-cloud environments, and within SaaS-based services—traditional centralized IT infrastructures and siloed business processes lack the end-to-end visibility required to effectively and efficiently monitor all of the complex interactions between and among distributed applications.
Second, the center of data gravity is moving. Enterprises are now placing data at the edge in order to keep it closer to the users and applications. Movement of this data to the edge requires careful design. Beyond ensuring proper management and distribution of this data, considerations need to be given to data security and privacy. Architects need to design solutions that mask data from potential exposure and ensure proper access controls to that data. Sensitive data should be moved to the edge with encryption in place, as well as access controls to ensure only authorized users and systems have access to that data.
Third is the increased operational overhead to ensure consistency of policy, especially if organizations deploy different access control points in different environments. Access policies shouldn’t change, after all, whether a given app is in Amazon, Azure, Google, or the data center. It's access to the app that matters, not where that app resides. Differences in the access control point deployed to stand guard for an application can lead to mismatched policies that result in unauthorized access or compromise.
Consistency of policy across multiple cloud properties has been the top challenge facing organizations for as long as we've been asking about multi-cloud challenges. The recent diaspora of applications and access control only serves to exacerbate the importance of implementing a unified access control point able to enforce a consistent set of access policies.
The good news is such a unified access control point exists. Equinix is the ideal location to deploy security control points, allowing for consistent policy enforcement in a multi-cloud world. Deployed at a strategic location within Equinix, F5’s Access Manager provides the control point organizations need to realize the required consistency to reduce costs and the risk of compromise.
F5 Access Manager
When moving workloads to the cloud, controlling access to and enforcing the same security policies for applications is critical to maintaining a positive security posture and protecting sensitive customer and corporate data. Organizations need to control who has access, to what applications, from which networks—down to the device level. Perhaps my access to a restricted app is based on whether or not my client is running the latest anti-virus software. Perhaps it's based on my browser, or even my location. Access control services must be flexible enough to support a broad range of variable-based access without being overly complex to create policy.
Operators also need to provide features such as SSO as well as institute security frameworks such as a zero-trust model. By leveraging F5 Access Manager, operators can add various levels of access control, including policies that determine which users can go to which applications in which cloud (public or private), regardless of which network the application resides on. Access Manager is a secure, flexible, high-performance access management proxy solution that provides unified global access controls.
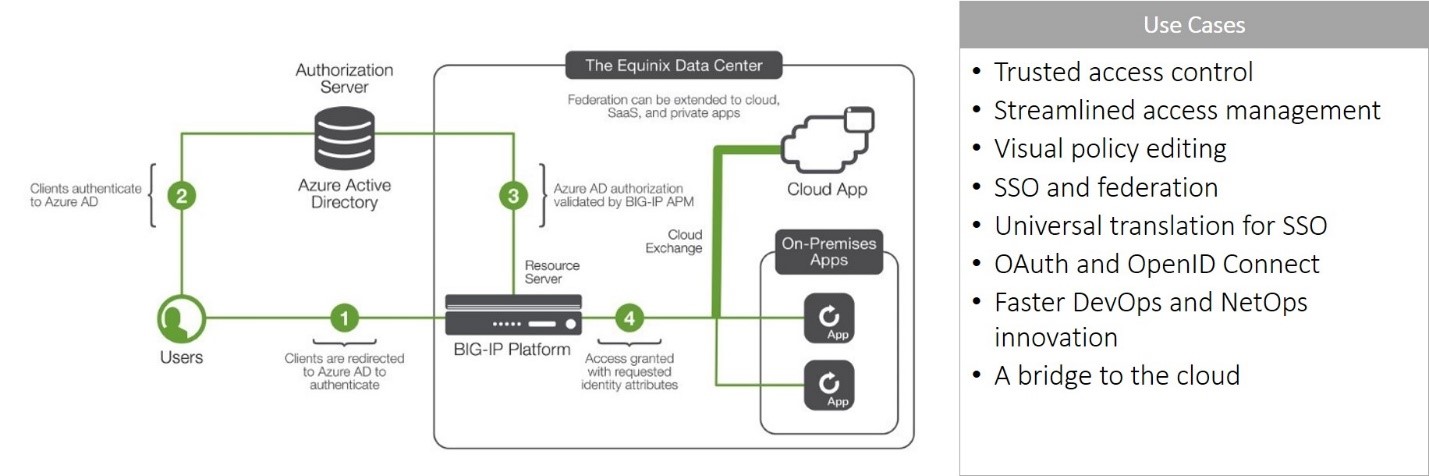
F5 Access Manager's visual policy editor makes it easy for operators and security professionals to design the right policy without learning a complex policy language. It provides access control for custom applications and SaaS application alike and supports SSO to ensure users experience less friction while working from anywhere.
The benefits of using F5 Access Manager in Equinix to enforce centralized access policies include:
- Optimized Cost Efficiency. Cloud resources are not consumed unless the user and request has been inspected and cleared of malicious content/intent. Cloud costs are kept under control by rejecting unauthorized access.
- Simplified Operations. A single access control point reduces operational overload caused by multiple dashboards, consoles, logs, and policy languages.
- Improved Security Outcomes. The centralization of access control enables consistent policies that cover all applications. Consistency of policy and enforcement is key to improving the security posture of the business and stopping credential-stuffing attacks from succeeding.
There are more benefits to employing F5 solutions in the Equinix environment. If you missed them the first time, here are more resources you can check out to learn more:
- Equinix Technology Alliance
- Equinix & F5: Taking Control Of Your Hybrid Cloud Security
- Improving Business Outcomes and Application Experiences with a Cloud Gateway in Equinix
- Improving Security Outcomes with F5 SSLO in Equinix
Stay safe!
